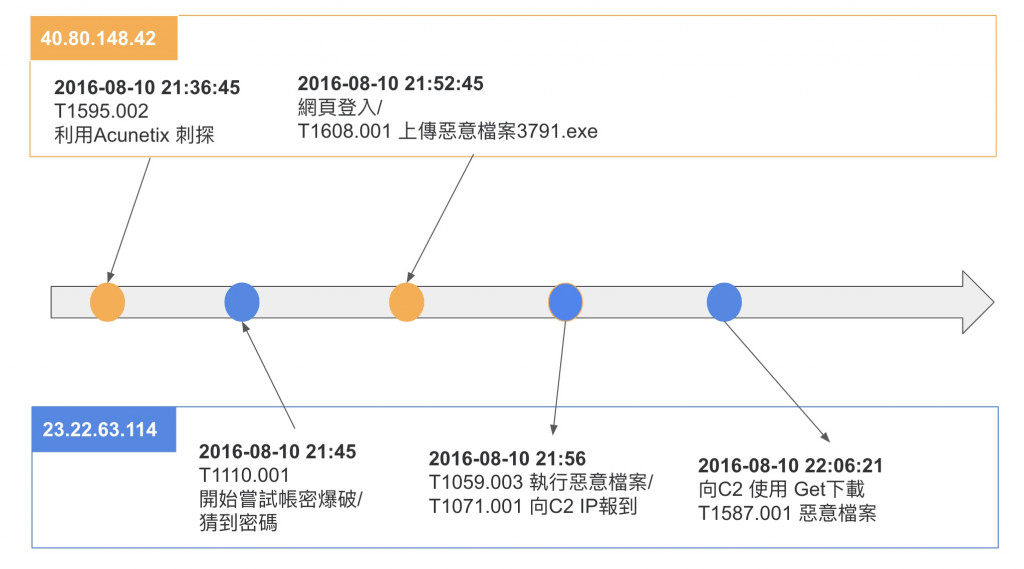
利用Acunetix 刺探
Reconnaissance
T1595.002 Active Scanning: Vulnerability Scanning
https://attack.mitre.org/techniques/T1595/002/
開始嘗試帳密爆破
Credential Access
T1110.001 Brute Force: Password Guessing
https://attack.mitre.org/techniques/T1110/001/
上傳惡意檔案
Resource Development
ID: T1608.001 Stage Capabilities: Upload Malware
https://attack.mitre.org/techniques/T1608/001/
執行惡意檔案
Tactic: Execution
ID: T1059.003 Command and Scripting Interpreter: Windows Command Shell
https://attack.mitre.org/techniques/T1059/003/
向C2 IP報到
Tactic: Command and Control
ID: T1071.001 Application Layer Protocol: Web Protocols
https://mitre-attack.github.io/attack-navigator/
下載惡意檔案
Resource Development
ID: T1587.001 Develop Capabilities: Malware
https://attack.mitre.org/techniques/T1587/001/
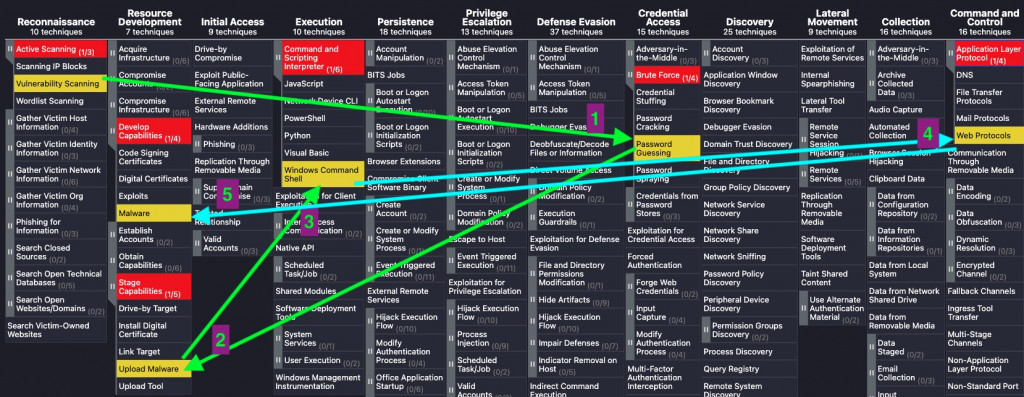
可以參考Exercise2 練習
https://attack.mitre.org/resources/training/cti/